
Cybersecurity Awareness at DCU
Cybersecurity awareness is essential for DCU staff & students to protect the university from the significant risk of cyber-attack.
As cybercriminals become more sophisticated and attacks become increasingly prevalent, the need for cybersecurity training and awareness has never been greater!
We ask that you take the time to view the information below on the following cyber threats; Phishing, Ransomware, Malware, Vishing, Smishing, Malvertising.
What is Phishing?
Phishing refers to different types of online scams that ‘phish’ for your personal and financial information, such as:
- Passwords.
- PPS numbers.
- Bank account information.
- Credit card numbers.
- Usernames & Passwords.
- Personal Information
These communications claim to come from a legitimate source: a well-known software company, online payment service, bank, or other reputable institution. Some will use an organisation's email address, logo, and other trademarks to fake authenticity. Phishing messages may also appear to be from a trusted friend or colleague.
Phishing communications can come from a growing number of sources, including:
- Phone calls
- Fraudulent software (e.g, anti-virus)
- Social Media messages (e.g., Facebook, Twitter)
- Advertisements
- Text messages
Signs of phishing include:
Ultimatum: An urgent warning attempts to intimidate you into responding without thinking. ‘Warning! You will lose your email permanently unless you respond within 7 days’.
Incorrect URLs: Scammers may obscure URLs by using hyperlinks that appear to go to a reputable site. Hover your mouse over any suspicious links to view the address of the link. Illegitimate links often contain a series of numbers or unfamiliar web addresses.
No signature or contact information: Additional contact information is not provided.
Too good to be true offer: Communications about contests you did not enter or offers for goods or services at an unbelievable price are likely fraudulent.
Style inconsistencies: Pop up windows that claim to be from your operating system or other software may have a different style or colors than authentic notifications. Communications that claim to be from a reputable organisation may be missing branding aspects such as a logo.
Spelling, punctuation, or grammar errors: Some messages will include mistakes. ‘Email owner that refuses to update his or her Email, within Seven days’
Attention-grabbing titles: "Clickbait" titles (e.g., "You won't believe this video!") on social media, advertisements or articles are sensationalist or attention-grabbing and sometimes lead to scams.
How to report a Phishing email from your DCU a/c
It is possible to report a Phishing email from your DCU mail a/c; follow the steps below:
- Click on the drop-down burger menu, circled in red on the right of the page.
- When the menu expands, click on the Report Phishing option.
- This will automatically report the instance of Phishing to Google.
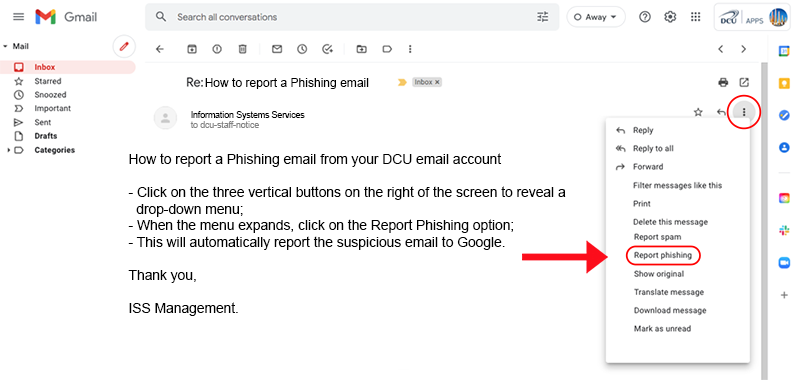
How to report a phishing email
What is Ransomware?
Ransomware is a Malware/Virus that stops you from using your PC. It holds your PC or files for ransom. Ransomware can make its way onto a system through various means, with the victim ultimately downloading and installing a malicious application.
Once on the device, the malicious application will spread throughout the system and encrypt files on the hard drive or simply lock the system itself. In some cases, it may block access to the system by displaying images or a message across the device’s screen to persuade the user to pay the malware operator a ransom for the encryption key to unlock the files or system.
What does it look like and how does it work?
There are different types of ransomware, however all of them will prevent you from using your PC normally, and they will all ask you to do something before you can use your PC.
They can:
- Prevent you from accessing Windows.
- Encrypt files so you can't use them.
- Stop certain apps from running (like your web browser).
They will demand that you do something to get access to your PC or files.
- Demand you pay money.
- Make you complete surveys.
- There is no guarantee that paying the fine or doing what the ransomware tells you will give access to your PC or files again.
Advice
Avoid opening any attachment emailed to you that you were not expecting or can not be verified from a known source.
Watch out for emails with attachments suggesting you must reply quickly or 'act fast' and hence, feel compelled to open the attachment quickly - without considering the source.
It’s essential to check the content of the messages you receive by email. As well as the content of emails, their attachments have become a widespread method for propagating malware, which is one of the main means of infection by ransomware.
For this reason, practices like checking the sender message, taking care of offers that sound just too tempting to resist, checking that it is really an email that has been sent, and not clicking on suspicious links are basic measures to take in order to avoid falling victim to tricks that might result in infection.
For the record, we are Information Systems Services (ISS) and any communication from us should be personally signed – if in doubt, look up the sender from the DCU phone directory: http://www.dcu.ie/info/staff.shtml
What is Malware?
Malware, also known as malicious software, is a term used to describe malicious programs installed on end-user systems and servers, commonly known as a computer virus.
They are designed to disrupt, disable, or take control of a computer system using clever techniques to trick users.
The most common types of malware are:
Ransomware - locks a system until the victim pays a ransom to unlock it
Credential Stealers - acquire usernames and passwords for accounts
Banking Trojans - target banking information, such as usernames and passwords
Keyloggers - record keystrokes to get passwords and account numbers
Rootkits - allow attackers to get control of systems Malware attacks are activated by tricking people into opening an infected file or clicking unsafe links, which not only put computers at risks, but also entire networks within organisations.
What is Vishing?
Vishing (Voice Phishing) is the fraudulent practice of making phone calls or leaving voice messages purporting to be from reputable organisations in order to induce individuals to reveal personal information, such as bank details, passwords, and credit card numbers.
As with other kinds of phishing, voice scams rely heavily on manipulation and social engineering to get victims to give up personal information.
With Vishing, criminals typically pretend to be from an official source, such as a bank or government organisation.
Most Vishing attempts try to convince the victim to give up PIN numbers, PPS numbers, credit card security codes, passwords, or other personal details. That information will then be used for identity fraud or later steal money directly from an account. In some cases, the Vishing scammer will attempt to gain access to personal or financial accounts (such as a bank account) in order to steal information or money.
Not all Vishing scammers target individuals
One common misconception about Vishing is that the attacks target average consumers. However, businesses are also common in crosshairs. Scammers may target businesses to obtain private user information and potentially scam those businesses out of money and valuable data.
Types of Vishing
Common types of vishing you’re likely to run into involve:
Supposed fraud or suspicious activity on your bank account
Overdue or unpaid taxes to the Internal Revenue Service (IRS), HM Revenue and Customs (HMRC) or other tax agencies
Prize or contest winnings (such as a cruise or an “all expense paid” vacation)
Fake computer tech support calling to remotely access your PC to fix a problem
Faked government agencies (such as a court or law enforcement agency)
For businesses, Vishing scammers may be more likely to put real people on the line. The scammers may warn about fraudulent or suspicious bank transfers or pretend to represent some form of computer or IT support service. The goal is to gain access to financial account information or gain remote access to computers.
How to avoid vishing scams
Never give personal information over the phone.
Information Systems Services will never ask for your password over the phone.
Banks and government institutions should never ask for personal information over the phone.
That said, banks will call you if they believe fraud may be occurring on your account. However, they will typically only call to confirm your location and alert you to the event. They won’t ask for private information in a call you receive from them. Government institutions like the IRS almost exclusively communicate by mail or occasionally email to conduct official business.
If you are asked to give personal information, politely decline and end the call. If you are worried that you may have been a victim of an attempted Vish or would like some advice, please contact Information Systems Services.
Smishing (SMS Phishing)
Smishing is conducted via Short Message Service (SMS), a telephone-based text messaging service.
A Smishing text attempts to entice a victim into revealing personal information via a link that leads to a phishing website.
While some might recognise this as a scam, many unsuspecting users would not.
If you are worried that you may have been a victim of an attempted Smish or would like some advice, please contact Information Systems Services.
Malvertising, what is it?
Malvertising is the name the security industry give to criminally-controlled adverts which intentionally infect PCs. These can be any ad on any site – often ones you use as part of your everyday Internet usage.
The first sign will often be when the malware is already installed and starts threatening money for menaces, logging your bank details or any number of despicable scams.
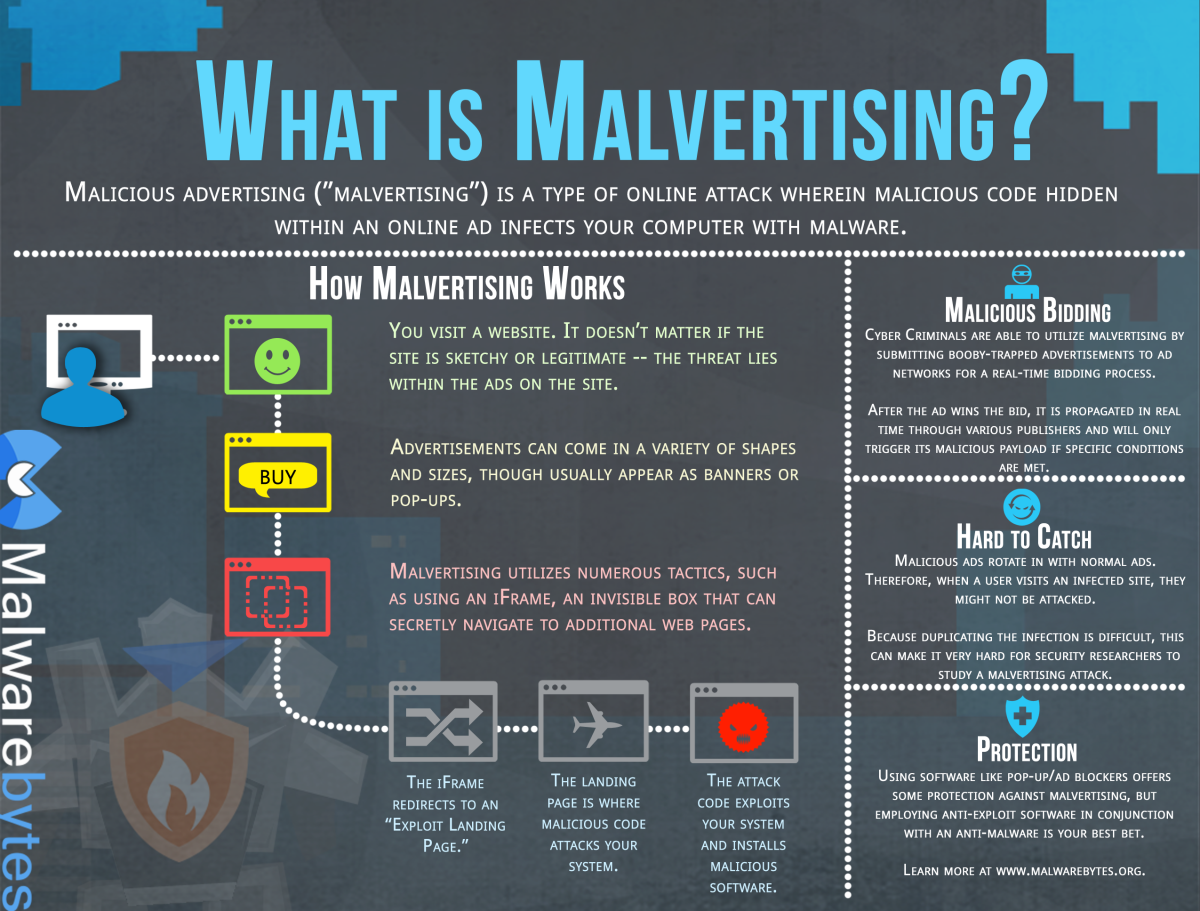
Malvertising
How do they get there?
It’s common practice to outsource the advertising on websites to third-party specialists. These companies re-sell this space and provide software that allows people to upload their own adverts, bidding a certain amount of money to ‘win’ the right for more people to see them.
This often provides a weak point, and cybercriminals have numerous clever ways of inserting their own malicious adverts into this self-service platform. Once loaded, all they have to do is set a price per advert to compete with legitimate advertisers and push it live.
Why is it a threat to me?
Today, we are aware of practices that look or feel ‘wrong’ on the Internet, be it odd-looking links, requests to download strange programs or posts on social media, which set the alarm bells ringing. The real danger with Malvertising is that user judgement isn’t involved at all. People don’t have to click anything, visit a strange website or follow any links.
Rather, you go to a website you trust (like a news site or similar), and the adverts are secretly injecting criminal software onto your computer. This means infections can happen just by browsing the morning headlines, visiting your online dating profile or watching a video.
How to protect your digital environment?
If you receive a suspicious email
Do not reply, even if you recognise the sender as a well-known business or financial institution. If you have an account with this institution, contact them directly and ask them to verify the email's information.
Do not click any links provided in these emails (or cut and paste them into a browser). This may download viruses to your computer, or at best, confirm your email address to phishers.
Do not open any attachments. If you receive an attachment you are not expecting, confirm with the senders that they did indeed send the communication and meant to send an attachment.
Do not enter your personal information or passwords on an untrusted Web site or form referenced in this email.
Report any suspicious messages that claim to be from DCU or contain a suspicious attachment or link to Google via the Report Phishing option located on the right side of each email beside the Reply option. See phishing section above for details on how to report a phishing email.
Use security best practices
Use your DCU password exclusively for your DCU a/c.
Use a unique password for each of your online accounts.
Never use the same password for multiple accounts.
Run a full virus scan of your computer every month. To detect the latest viruses, you must use a current version of your anti-virus software and keep it updated.
ISS recommend that you use MacAfee which actively checks your computer for anti-virus software, firewall protection, and web security, and threats in your open applications.
Contact ISS for a licence of MacAfee.
Update your device's operating system with the latest security patches, including your mobile operating system.
Use Windows Update (Windows) or Apple Software Update (Macintosh) and enable automatic updates to receive security patches as soon as they are released.
Keep your software updated, especially your Web browser, mobile operating system, Adobe Reader and Flash Player.
Restart your computer at regular intervals: ISS recommend that you reboot your computer at regular intervals to ensure that all software patches are deployed, installed and functioning correctly.
Backup your data to Google Drive
Backup all you data to Google Drive at regular intervals using Google Drive. It is possible to restore all your data from Google Drive in instances of Ransomware. ISS recommends that you create two backup copies; one to be stored in the cloud and one to store physically, in a portable hard drive, thumb drive, extra laptop, etc. Backup copies will also come in handy should you accidentally delete a critical file or experience a hard drive failure.
Google Drive Features
Upload Files for Storage: Receive unlimited free storage with DCU Apps.
Share Files: Share files with friends and co-workers easily with DCU Apps Drive.
Google Docs: When using Drive via your web browser you will have access to the Google Docs suite.
Google Drive: Upload and store files from any folder on your computer, camera, and SD cards to Google Drive.
Google Drive Desktop: Allows you to quickly access all of your Google Drive files on demand, directly from your computer without losing precious drive space.
